Workflow-based and Object-based Security
Access control comes in two forms: workflow-based and object-based. The type of access control you use is a matter of preference, but is generally influenced by how your datasource is set up.
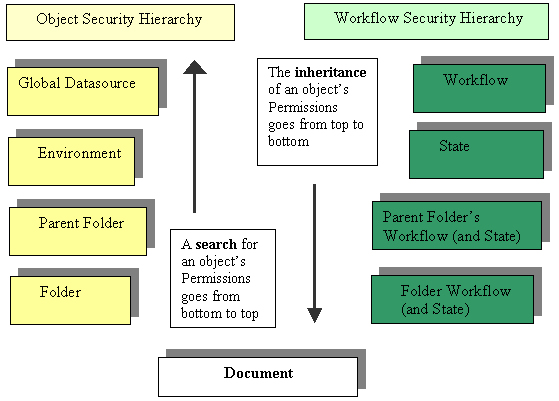
If your datasource is workflow driven, you can use a workflow-based approach to access control, also referred to as workflow security. For example, workflow1 has stateA, stateB, stateC, and stateD. In ProjectWise Administrator, you can set workflow1 to only be accessible by certain users in the datasource. Then you can set which of those users have access to each state in the workflow, and what permissions each user has for folders or documents in that state (for example, read-only, read/write). When workflow1 is assigned to a folder in ProjectWise Explorer, the folder and document security you defined for workflow1 will automatically be applied to the selected folder and its documents.
If your datasource is not workflow driven, you can use an object-based approach, also referred to as object security. In this approach, folder and/or document permissions can be set for the entire datasource in ProjectWise Administrator. Any folders, subfolders and documents in ProjectWise Explorer will inherit these permissions. At any level in ProjectWise Explorer, new permissions can be set which the lower levels inherit. As each new level is created it automatically inherits the permission set from the previous level. This permission set can then be edited and will become the object's own permission set.
The two approaches are independent and only merge when a question of access rights to a particular document or folder must be resolved. If an object has no security items defined for itself, it inherits the security items from the first object up the hierarchy that has defined items.